Red team engagements are becoming more and more popular and system administrators are more aware about tools and techniques so avoiding detection is a much harder task. Red teamers from the other hand are always looking for command and controls tools that are using either legitimate traffic or standard functionality of Windows to hide their activities. The native Windows Script Host engine can be used as another method of command and control as it was presented at Bsides Las Vegas 2017 and a tool was released to assist towards this activity.
Koadic Framework was developed by Sean Dillon and Zach Harding and is based in JavaScript and VBScript since it is using Windows Script Host (WSH). Therefore it can be used in multiple Windows environments from Windows 2000 to Windows 10. Legacy systems they don’t have PowerShell or they might be running an old version of ASP.NET so compare to other tools that are based in PowerShell it can be used as a more reliable solution.
Koadic is fast, less noisy and has the ability to deliver payloads in memory as well.
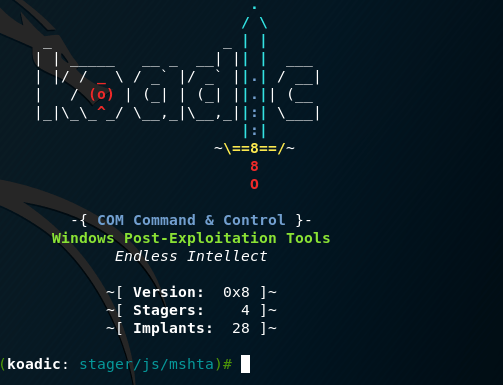
Koadic by default is configured to use Microsoft HTML Application as a stager and the only requirement is to set the local IP address. Other stagers involve the usage of rundll32 and regsvr32. Additionally as many other command and control tools it supports encrypted communication for a more stealthy approach.

The following command needs to executed on the target from a command prompt:

By specifying the Zombie ID Koadic can interact with the host:

Koadic is using some of the well-known user account control (UAC) bypasses of Matt Nelson to perform elevation.

A new session will created but this time it will be elevated:

It is also possible to execute commands on the target by using the cmdshell and the zombie ID.

This framework has a number of implants that can be used to execute various activities like:
- Gather password hashes
- Bypass UAC
- Perform a port scan
- Kill antivirus
- File transfer
- Execute shellcode
- Perform Phishing

Performing a port scan on a number of targets is easy with the following implant:

Open ports will appear in green:

It is also possible to attempt to steal password from normal users through a password box. However this will defeat the purpose of being stealthy during the red team engagement.
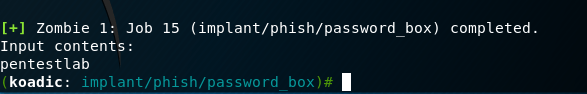
The script prompt that will appear to the user:
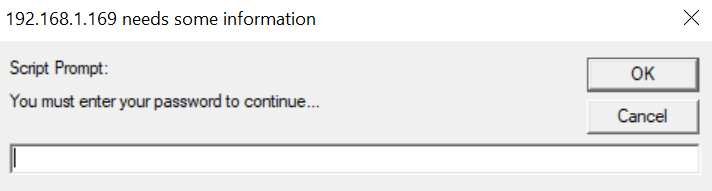
- Koadic – Script Prompt
Reference
https://github.com/zerosum0x0/koadic
Click to access DEFCON-25-zerosum0x0-alephnaught-Koadic-C3.pdf
Wow great stuff!