Mobile application penetration tests go beyond the standard discovery of vulnerabilities through Burp Suite. It is vital to know how to decompile the application for the examination of vulnerabilities into the application code. The purpose of this article is to demonstrate various techniques and tools of how to reverse engineer an android application.
In order to start the reversing process the APK file of the target application is needed. Usually the client is responsible to provide this file to the penetration tester. However if for whatever the reason this is not possible then this article explains various methods of how to retrieve the APK file from Google Play Store and from the actual device.
The APK File
Android Application Package (APK) files are the files which are used by the Android operating system for distribution and installation of mobile applications. Typically an APK file is just a zip file which has been renamed as an APK in order the Android operating system to recognize it as an executable. The unzip utility can be used to extract files that are stored inside the APK.

Every APK contains the following files:
- AndroidManifest.xml // Defines the permissions of the application
- classes.dex // Contains all the java class files
- resources.arsc // Contains all the meta-information about the resources and nodes

Contents of an APK File
Alternatively other tools can be used as well to decompile an android application. The d parameter instructs the apktool to decompile the APK.

Another method is to try to convert the actual .APK file into .JAR and then use any tool that can decompile java code.
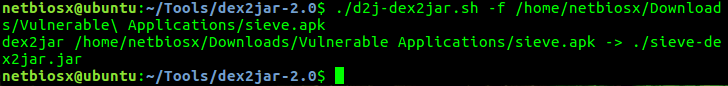

Extraction of APK files can be done also with the Android Asset Packaging Tool.

Jadx is another tool which can produce Java source code from Android APK and DEX files.

Android Manifest
The android asset packaging tool can be used to obtain the manifest file of an APK application.

As the output above is not easy readable the following command can dump only the permissions of the application.

Alternatively if the contents of the APK file are already extracted then a more specialized tool like AXMLPrinter can be used to read the XML file in a more elegant way.

Drozer can also parse the manifest files of installed applications:
dz> run app.package.manifest com.mwr.dz <manifest versionCode="5" versionName="2.3.4" package="com.mwr.dz"> <uses-sdk minSdkVersion="7" targetSdkVersion="18"> </uses-sdk> <uses-permission name="android.permission.INTERNET"> </uses-permission> <application theme="@2131165185" label="@2131099648" icon="@2130837513" debuggable="true"
Extensive information of how to assess Android Manifest files can be found in this article.
Classes DEX
The classes.dex file contains all the java classes of the application and it can be disassembled with baksmali tool to retrieve the java source code.


DEX files can be also disassembled into Dalvik instructions:

MobSF
The mobile security framework is all in one suite that can be used to perform static and dynamic code analysis for Android, iOS and Windows phone applications. MobSF automates the process that is has been described in this article as it can decompile the APK, read the manifest file, identify issues in the source code and in the Manifest file, extract the certificate of the application etc.
The image below demonstrates the analysis of an APK file via the mobile security framework:
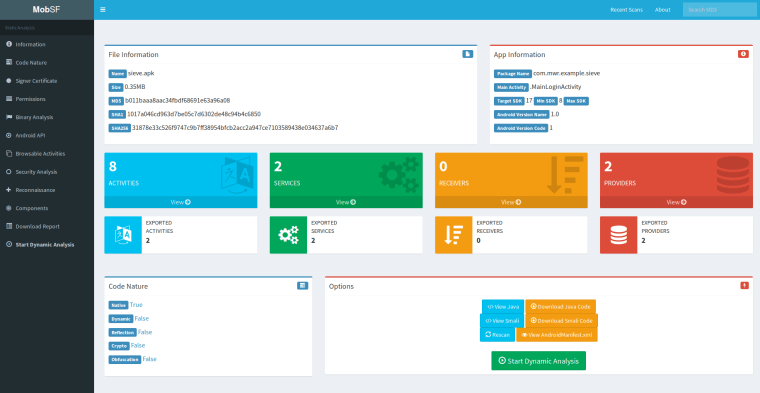
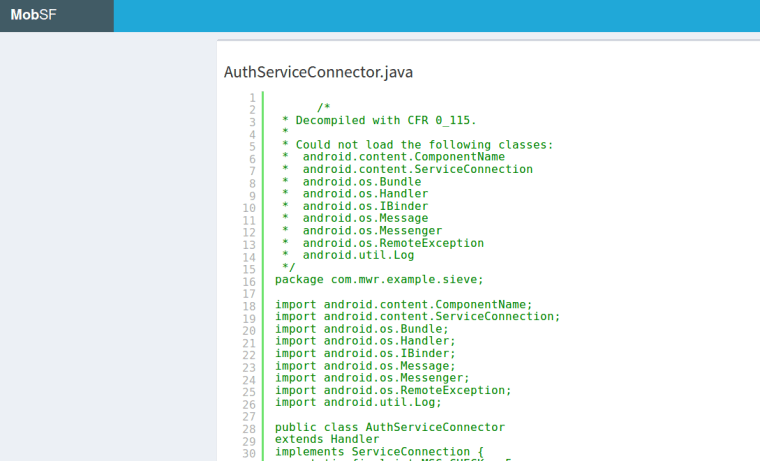
From the moment that the APK is uploaded the framework decompiles the application automatically so it eliminates the need for further tools.
The official GitHub repository of the tool is: https://github.com/MobSF/Mobile-Security-Framework-MobSF
Summary
Reverse engineering an android application can give an understanding of how the application really works in the background and how it interacts with the actual phone. This knowledge would assist in the process of discovery vulnerabilities that exist in the code and are not obvious.
Reblogged this on KNX Security – Practical Penetration Test.