In many occasions as a penetration testers we will have to face a web application where it will contain a login form which we will have to test it for weak credentials.Burp Suite is probably the best tool to be used when assessing web applications.Burp’s main use is to be a proxy interceptor,however provides a lot of other functions to penetration testers and it can also be used to attack a login form.In this article we will examine how we can use Burp in order to perform a brute force attack on a web application.
Let’s say that we have the following login form:
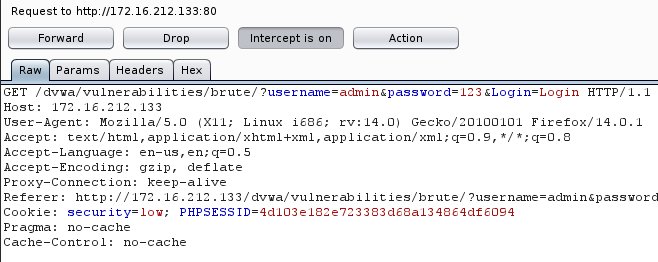
We will try to submit a username and a password and we will use the Burp Suite in order to capture the HTTP request.
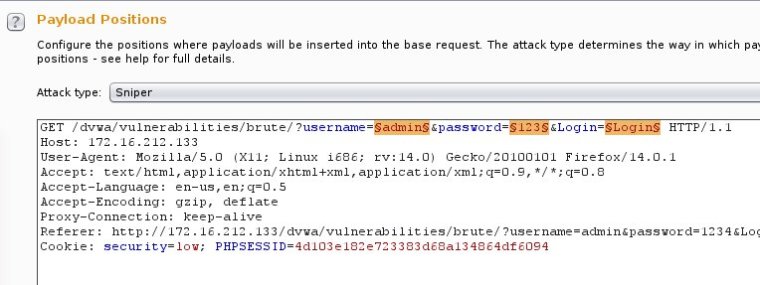
Then we will send the request to the Intruder (Action—>Send to Intruder) and we will clear the positions on the request that we will not need to insert payloads which are the $low$ and session cookie.So we will leave the following positions:
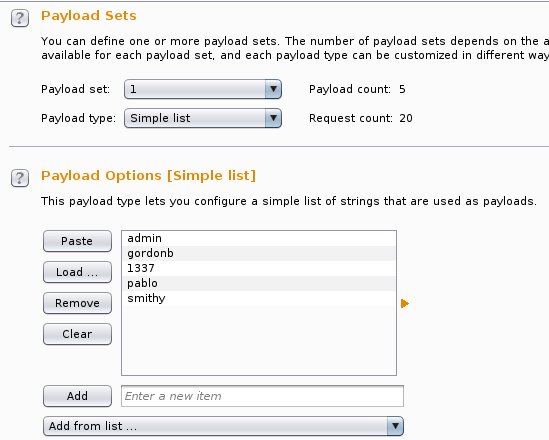
As an attack type we will choose the cluster bomb because this type of attack it can take each word of the username list and it can run it against each word of the password list in order to discover the correct credentials.
Now it is time to set the payloads on the three positions.So we will load our wordlists that contains usernames and passwords in the payload options of Burp and for the 3rd position we will just put as an option $Login$.In the next three images you can see this configuration.


Everything now is ready and we can start the attack on the Intruder.The Intruder will start sending HTTP requests to the form based on our payloads and it will try all the possible combinations.

After the inspection of the responses we will notices that Burp has successfully logged in under the credentials smithy/password.
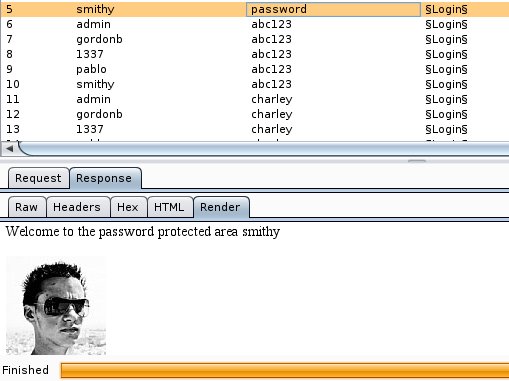
We can now go back to the application and to try to get access to the admin area with this username and password.

Conclusion
As we saw in this post Burp is also capable to perform brute force attacks against web applications.Login forms can be found almost in every web application and the intruder tool can help the penetration tester to automate his tests.The discovery of valid administrator credentials can make the difference in black-box penetration tests.
Why are you leaving the login field as a variable but then using a static value in it? May as well remove it from the list.
What’s new in this attack?!
There is nothing new in this attack Yuval.It is just a demonstration of how you can use Burp to perform this type of attack.
The Payload for Brute force can be SQL injection vectors in username and Password with Cluster Bomb.
Couldn’t you just use THC-Hydra?
No bloated GUI is needed then.
Burp is much better and a lot more powerful, I wouldn’t bother with anything else
Here’s the steps:
http://seclists.org/pen-test/2008/May/114
I see a software at http://www.eguardo.com . Interestingly they provide an API to stop brute force attacks on Microsoft.NET, PHP and Java. I tried and working…