As a penetration tester there will be times that the client requirements will be to perform social engineering attacks against their own employees in order to test if they follow the policies and the security controls of the company.
After all if an attacker fails to gain access to a system then it might try alternative ways like social engineering attacks.
In this post we will see how we can use the Credential Harvester Attack Vector of Social Engineering Toolkit in order to obtain valid passwords.
The first thing that we need to do is to attach our laptop into the network of the company that we need to do the Social Engineering Attack.When our system obtains a valid IP address from the DHCP Server we are ready to launch the attack.
We are opening SET and we will see the following options:

Our choice we will be the Website Attack Vectors because as the scenario indicates we need to test how vulnerable are the employees of our client against phishing attacks.In the next screenshot we can see the attacks that we have in our disposal.
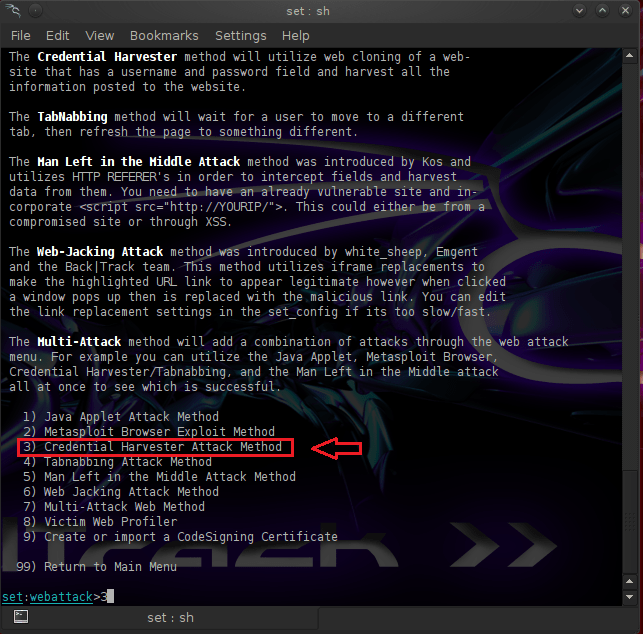
We will use the Credential Harvester Attack Method because we want to obtain the credentials of the users.As we can see in the next image SET is giving us 3 options.
For this example we will use the Site Cloner option in order to clone the login page of a very popular website that will have the role of the bait.
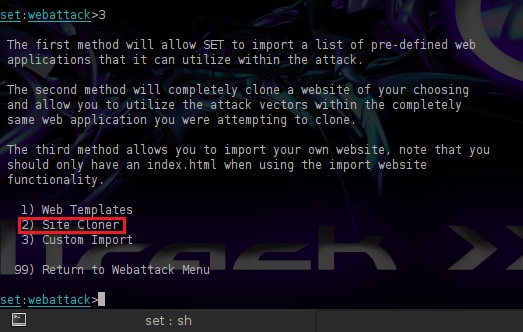
Now we are ready for the last setting,to choose the website that SET will clone.We have chosen Facebook because it is a well-known website,most of the employees of our client will probably have an account so it will be more easier to trick them.

The process of cloning the website Facebook have started and our machine is waiting to capture credentials from network users.

Now it is time to send our internal IP to the users in the form of a website(such as http://192.168.1.1.This) can implemented via spoofed emails that will pretend that are coming from Facebook and they will ask the users to login for some reason.
If a user reads the email and make a click to our link (which is our IP address) he will see the Facebook login page.
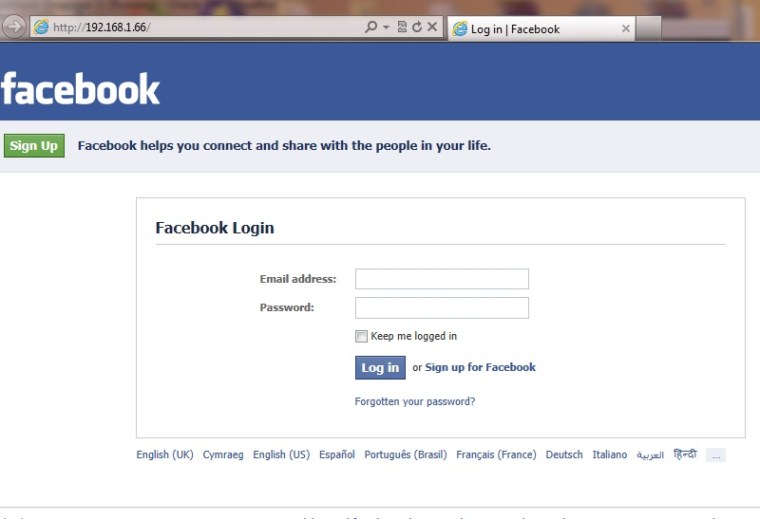
Lets see what will happen if the victim enter his credentials…
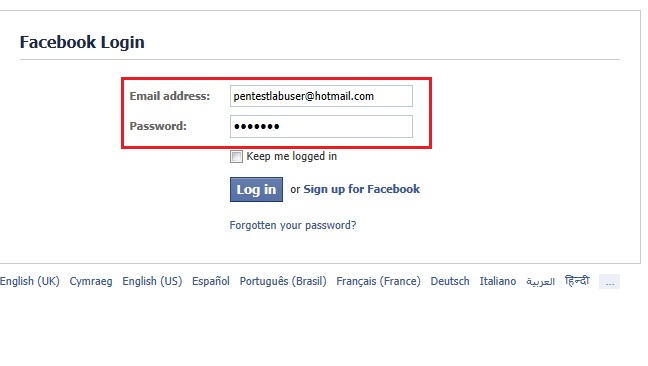
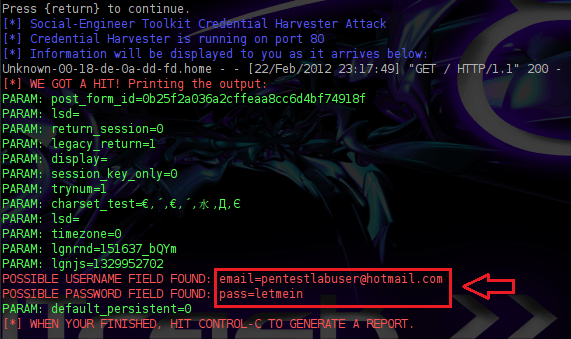
As we can see from the moment that the victim will submit his credentials into the fake website SET will send us his Email address and his password.This means that our attack method had success.
If many users enter their credentials to our fake website then it is time to inform our client to re-evaluate his security policy and to provide additional measures against these type of attacks.
Solutions:
In the scenario that the user would like to login with his account then our attack will have 100% success but even if the user will not login with his email and password the attack is still successful because the user have opened a website that came from an untrusted source.
This means that if the website had some sort of malware then it would infect the user computer because the user simply ignore the security policy of the company and opened an untrusted link.So the company must provide the necessary training to their employees in order to have a clear understanding about the risks.
Educating the employees is the key fact because even if your organization is using all the latest anti phishing software the employees could be the weakest link by opening a link that comes from an unknown origin.They must be aware about what is phishing,not to open any links and to put their details and to always check the address bar and things that would not look normal in order to avoid being scammed.
Always remember that a system administrator can patch a computer but there is no patch to human weakness.
I’m able to generate the email from BT to my inbox, but when I click on the link(https:192.168.88.xx (my BT IP and clonned facebook)) the cloned facebook page does not comeup. Am I missing something?
You should check if both your hosts (Backtrack and Victim) are on the same subnet.If not the clone website will not come up.
I like this
all steps is well but get / http/ 1.1” 200 not going a way how can get user or passw
@Jatinder kumar The user must enter his credentials into the fake form and then it will be returned to you.Otherwise you will not get anything.It is a very simpe attack to implement it.
How can I make this attack work when I am not on the same subnet as the users. I am doing a pen test for an external company. If I paste in my public IP, it should work right?
@Justin in order this attack to work externally you have got to go to the configuration file of SET and set the AUTO_DETECT option to Off.In that way SET will ask for your external IP.Also make sure that the port that SET is listening is open for outside connections.
indeed pastin our ip right then how can it be a safe attack from our side plus i think this works only with hotmail ids
@aaks you can buy a domain or a subdomain and in that way you can hide your IP and your URL will look valid.
Wow, thanks for the tutorial. I use no-ip on my router but how i can configure the SET of backtrack to the auto_detect mode off?
Thanks!
When i try to open my ip address in victim’s pc it doesn’t open!!!what should I do??plz help me!!